Abstract: In order to strengthen the public security prevention and control work, improve the predictability and accuracy of grassroots social security management work, and improve the efficiency of grassroots public security work, the public security management model needs to be transformed from traditional one-way management to two-way interaction, from offline mode to online and offline combination, and from government supervision to collaborative governance of the whole society. Therefore, it is necessary to establish an intelligent data center at the grassroots level and collect intelligent data of social resources within the jurisdiction. At the same time, the establishment of 5G virtual private network shortens the data access cycle and greatly reduces the transmission delay and cost.
With the acceleration of social development and urbanization, population mobility is becoming increasingly intense, and the social security situation is facing new situations and challenges. The traditional public security management model has gradually become unable to meet the new needs of maintaining social stability and public security, and it is unable to take the initiative in social security management. This is mainly reflected in two aspects:
First, it is difficult to manage key personnel, and the means of prevention and control are insufficient. The means of actively discovering high-risk personnel such as fugitives and wanted criminals are single. Such personnel are extremely dangerous and pose a security threat to police officers and managers in the jurisdiction. In addition, the high mobility of personnel and the complex composition of special groups have brought great difficulty and unprecedented pressure to public security work.
Secondly, there are information barriers between the intelligent equipment that have been built, and the data information between units is relatively independent, and the information has an obvious information island effect. For example, there is a large flow of people in a commercial entity in the jurisdiction, and there are many front-ends of the video surveillance system, but when the police work needs it, they must arrive at the scene to collect evidence, resulting in a waste of manpower.
At the same time, the alarm information of the intelligent video analysis of the monitoring system cannot be transmitted to the public security prevention and control department in the first time, and it is impossible to analyze, judge and deal with the incident in time. In addition, a large amount of raw data cannot be accumulated and analyzed, let alone summarized and shared.
1. Basic intelligent data center system
In view of the lack of prevention and control means and the “isolated island” of data resources, social security management, especially grassroots public security prevention and control work, needs to access more social resources to achieve the goal of “group prevention and group control”. Therefore, it is particularly important to establish district, county and street-level secondary data centers, with the following goals:
① Build a comprehensive security system to improve the daily prevention capabilities of the jurisdiction, and timely prevent, discover and respond to emergency incidents. By using modern computer technology, communication technology, Internet of Things technology, AI technology and automatic control technology, big data analysis will further improve the efficiency of “fighting, prevention, management and control” and promote lasting peace and harmony in the jurisdiction.
② Establish an intelligent infrastructure based on the ecology of various industries and a big data comprehensive public security management platform for mobile personnel and special groups. By collecting and integrating basic weak current data and relevant records of the activities of mobile personnel and special groups, and conducting diversified integration analysis with existing police system data, grid management data and other government information systems, the marginal effect of grassroots public security and stability maintenance forces can be maximized.
③ Realize interconnection with local public security organs’ social security video surveillance resources, and comprehensively improve the comprehensive social management and stability maintenance and emergency response capabilities of various business formats.
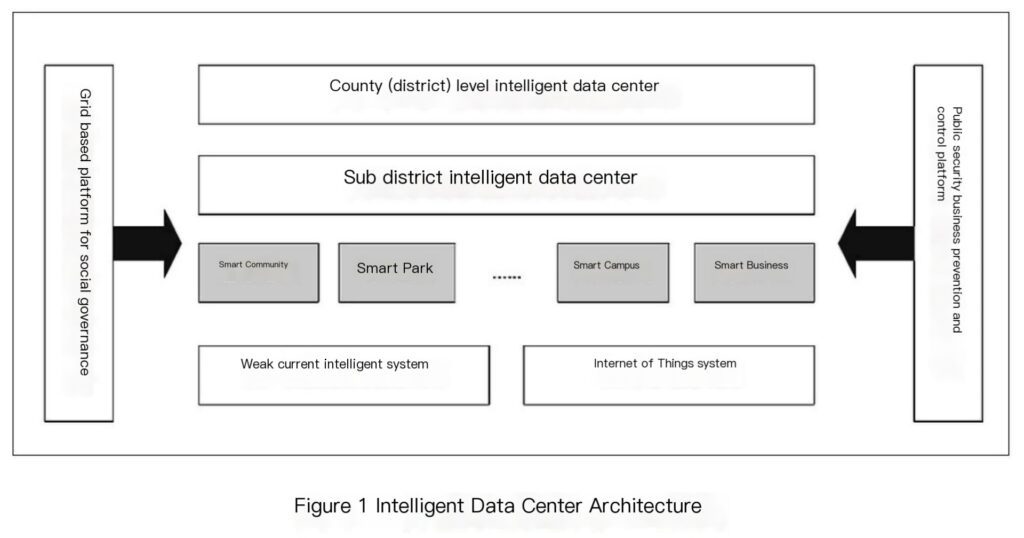
The county-level and street-level secondary intelligent data centers are mainly responsible for coordinating the construction of information platforms and data applications in the jurisdiction. These data can be used for social governance grid platforms, public security business prevention and control platforms, etc., to improve the utilization rate of data resources, innovate social security management capabilities, and enhance the foresight, accuracy and efficiency of social security management.
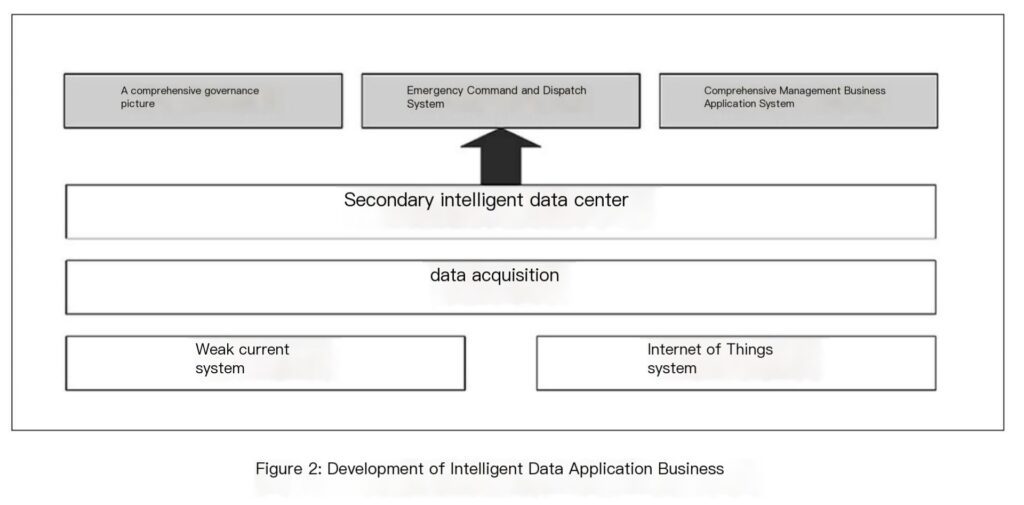
At the same time, application services can also be developed based on the collected data, such as a comprehensive governance map, and linked with the government emergency command and dispatch platform to build a social security management system of co-construction, co-governance and sharing, effectively improve the government’s management level and work efficiency, enhance the sense of gain, happiness and security of residents, and create a safe and stable social environment for the sustainable and healthy development of the economy and society in the jurisdiction. The architecture and business applications of the grassroots intelligent data center are shown in Figures 1 and 2.


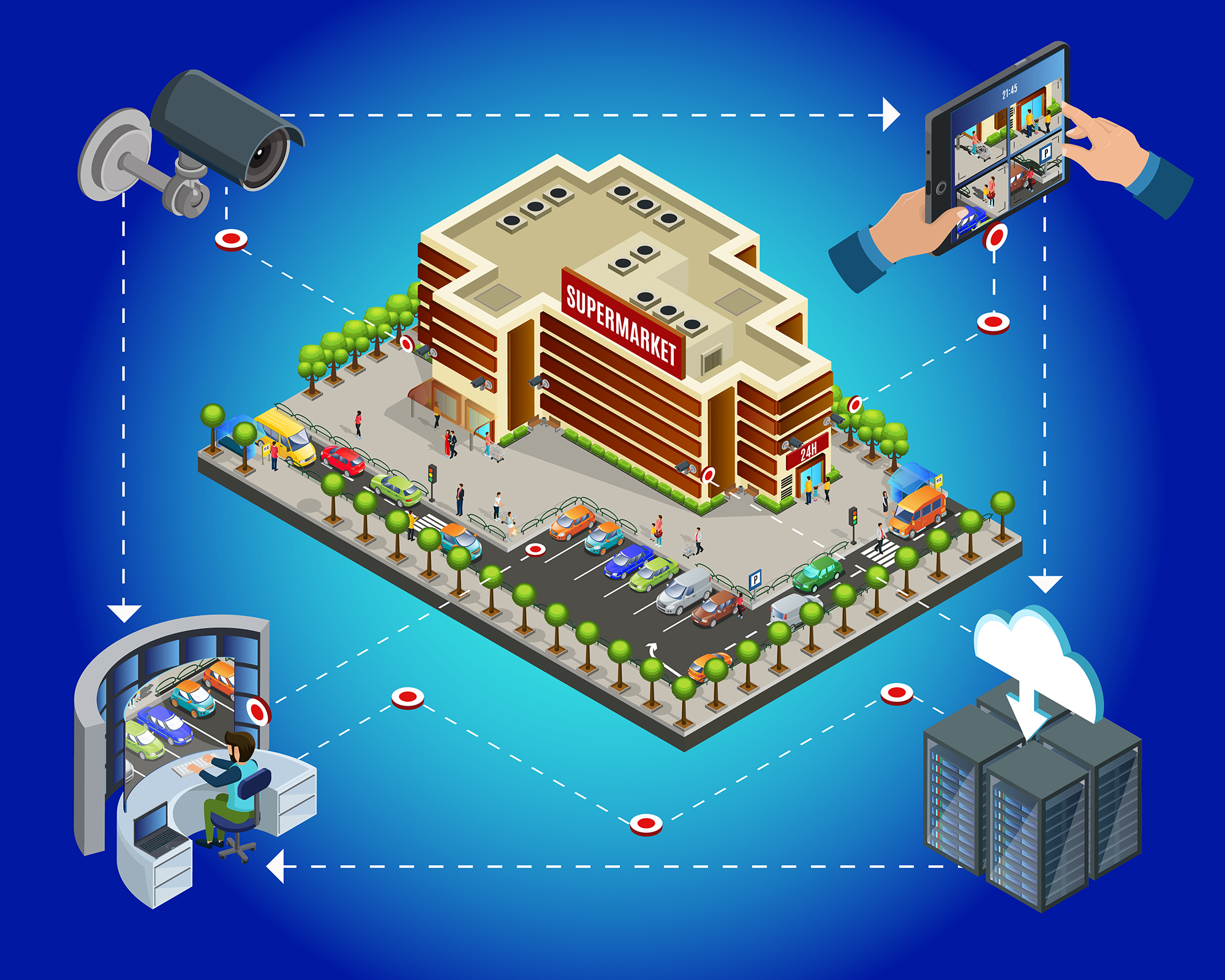
After the system establishes data access, it will control the following objects in the access area:
① Personnel control: Implement control over people entering and leaving the area, collect photos of key populations, people involved in stability, drug addicts, and released prisoners entering and leaving the area, establish files of daily activity content, track and record changes in behavioral status, and conduct statistical analysis to form a trajectory map of people’s whereabouts, so as to achieve prevention and control, and promptly discover and eliminate behavioral trends that endanger community public safety.
② Vehicle control: Collect and manage the entry and exit information and pictures of motor vehicles in the jurisdiction, and promptly discover and eliminate theft crimes. At the same time, link vehicle information to population information.
③ Public area security: unified management of intelligent equipment, collection and management of security information, infrastructure information, etc., timely discovery and notification of potential safety hazards, and intelligence analysis and incident handling.
However, in the grassroots intelligent data center system, data access in communities, commercial entities, etc. is often limited by network resources. For example, when laying optical cables for transmission, the cost is high and limited by optical cable pipeline resources; when fully using the public network for transmission, the network load is large, which will have a great impact on the real-time transmission.
2. 5G Virtual Private Network
Traditional public networks have certain limitations in meeting specific needs and providing high-quality services. Therefore, the construction of 5G industry virtual private networks has many advantages. First, it can provide high-speed, low-latency communication services to meet the needs of large-scale data transmission and real-time applications. Secondly, virtual private networks can be customized according to the characteristics and needs of different industries to provide more accurate and efficient network services. In addition, virtual private networks also have higher security and reliability, and can effectively prevent network attacks and data leakage risks.
1). Characteristics of 5G private networks
① Customization: 5G private networks can provide customized mobile communication services according to the needs of different industries and application scenarios, including network topology, frequency band resources, business functions, etc.
② High speed and low latency: 5G private network adopts 5G technology, which can provide high-speed, low-latency mobile communication services to meet the application requirements of high bandwidth and low latency.
③ High reliability: 5G private networks adopt a variety of technical means, such as multi-path transmission and data redundancy, to improve the reliability and stability of communications and ensure the continuity and stability of key services.
④ High security: 5G private networks implement a variety of security mechanisms, such as encryption, authentication, and access control, to ensure the security and privacy of data.
2). 5G private network model
5G private network is a private, customized mobile communication network built and operated by operators for specific industries, enterprises or organizations. Its main networking modes include the following:
① Independent networking mode (SA mode): This mode means that the 5G private network is completely independent of the public network and uses an independent core network and wireless access network. It can provide higher security and reliability and is suitable for industries with high requirements for network security, such as finance and government.
② Non-independent networking mode (NSA mode): This mode means that the 5G private network shares part of the network resources with the public network, using the core network of the public network and the wireless access network of the 5G private network, which can reduce the construction and operation costs to a certain extent. It is suitable for industries that do not have particularly high requirements for network security.
③ Hybrid networking mode: This mode refers to connecting the 5G private network with the public network through dedicated lines or VPN, which can not only meet the requirements for network security and reliability, but also reduce construction and operation costs. It is suitable for industries that have high requirements for network security and need to control costs.
In summary, the main networking modes of 5G private networks include independent networking mode, non-independent networking mode and hybrid networking mode, which can meet the needs of different industries and scenarios. For this system, considering the networking speed and economy, the use of hybrid networking mode is more in line with the requirements.
3. Construction Content
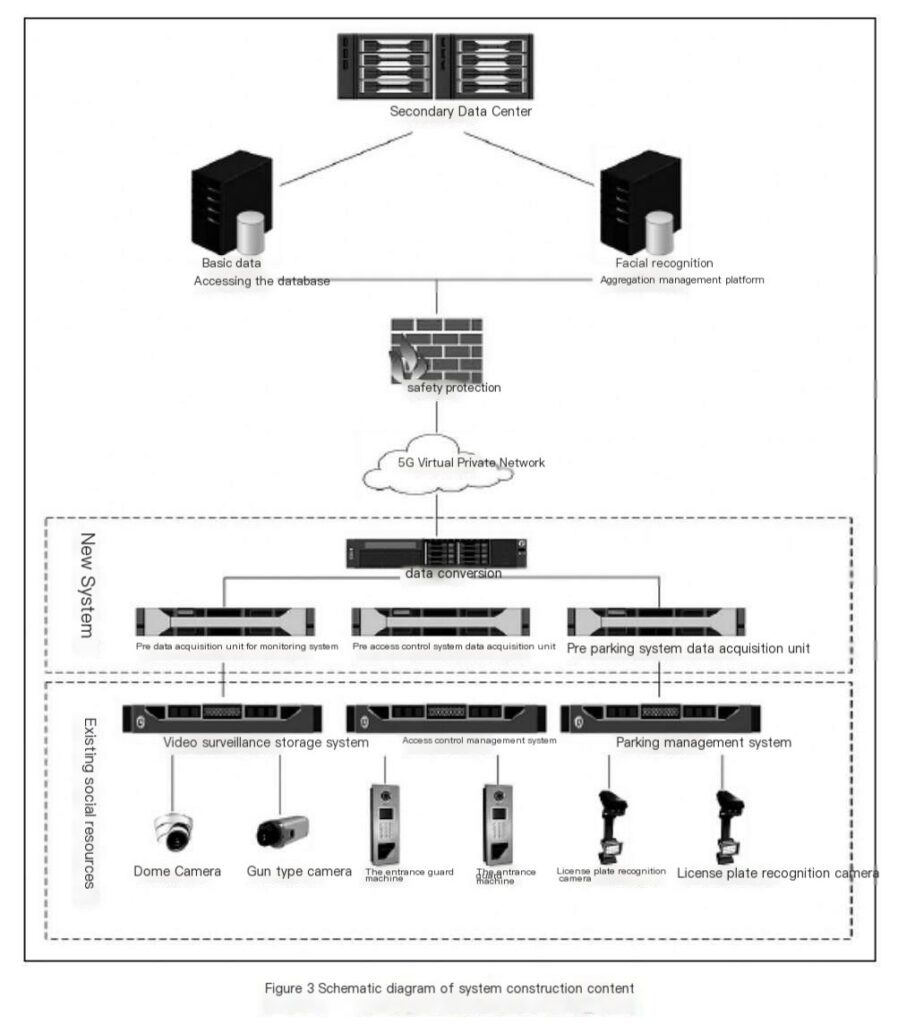
At present, the intelligent weak-current systems involved in the street-level jurisdiction mainly include video surveillance systems, access control systems, information release systems, public broadcasting systems, parking management systems, intercom systems, intelligent lighting control systems, passenger flow analysis systems, billing management systems, wireless Wifi systems, etc. According to the requirements of public security prevention and control at this stage, the following collection units can be set up in advance:
① Set up a front-end acquisition unit for the video surveillance system to uniformly manage the video surveillance system, connect it to the street intelligent data center system through a wired (wireless) data private network, provide video surveillance related data, such as real-time monitoring images of public areas, etc., and set alarms (reminders) for key personnel at the back end.
② Set up a front-end collection unit for the parking system, connect it to the parking lot management system, and connect it to the street intelligent data center system through a wired (wireless) data network to provide vehicle entry and exit related data.
③ Deploy a set of data conversion units to collect relevant data collected by the front-end acquisition unit of the video surveillance system and the front-end acquisition unit of the parking system, perform protocol conversion, and uniformly upload relevant basic data such as video, personnel entry and exit, and vehicle entry and exit to the intelligent data center platform.
This system collects business data from subsystems such as video surveillance, access control management, and parking management for various information infrastructures, realizes the new standardized construction of intelligent subsystem facilities, prompts the platform system to provide standardized basic data that meets access requirements, and builds a big data comprehensive public security management platform based on the intelligent infrastructure of various industry ecosystems and mobile personnel and special groups.
By collecting, sorting and classifying these intelligent basic data, and integrating and analyzing them with existing police system data, grid management data, and other government information systems, the effectiveness of grassroots public security management and stability maintenance forces can be maximized.
4. System Construction Principles
The construction principles of this system include mastering the forefront of technology, ensuring that necessary modules are complete, maintaining stable system performance, and achieving resource cost savings, so as to ensure that the intelligent data center can become an information system that meets the basic comprehensive application scenarios.
At the same time, comprehensive consideration is given to factors such as post-maintenance, convenience of on-site and back-end use, and appropriate room is reserved for system upgrades and expansions.
① Unification of practical principle and economic principle. First of all, the principle of practicality should be met. This system should meet the business needs of grassroots public security management as much as possible, meet the needs of operation and statistics of various personnel involved, and adapt to the development of related technologies in a long period of time.
On the premise of meeting these requirements, we should also try our best to save investment in system construction, select products with relatively mature technology, comprehensive functions and stable performance tests, and make full use of the equipment installed in the original system.
② Unification of advancement and rationality. The scheme design will strictly follow the relevant design standards and balance the rationality of the system and the advancement of technology. Look at the overall situation, pursue the scientific rationality of the entire system function, and do not blindly pursue the advancement of local indicators.
When the necessary functions and operating performance of the entire system are met, try to use mature technology, compatible and expandable, and have good development prospects.
③ Unification of standardization and openness. The layout of the system should be modularized and standardized to the greatest extent, and should be designed in strict accordance with international, domestic and industry standards to ensure the interconnection between subsystems and between the original system and the newly built system.
Since the lower-level sub-platform is built in phases, the future business development and system expansion of the system should be reasonably predicted under scientific premise during the design and selection stage of this system, and redundant expansion design should be carried out on this basis to fully reserve the corresponding space.
④ Reliability and security should be unified. The layout design of the entire system should be reliable and stable, and equipment with a higher security level and good stability should be selected. Redundant backup should be designed for key equipment or key parts of the system. The system software should have a complete security mechanism and a high security protection level to ensure that the dedicated network security products are reliable and fully functional.
⑤ Easy maintenance and easy management. The system should be easy to maintain and manage, and the infrastructure architecture design should be as simple as possible to reduce the cost of later system operation and maintenance and upgrades. In order to ensure the quality of after-sales service of the product, well-known brand products with mature technology should be selected.

4. Conclusion
The construction of grassroots intelligent data centers aims to solve the public security management problems faced by grassroots governments and their dispatched agencies in today’s urban development. The focus is on the difficulties of managing floating populations and key prevention and control groups, forming a multi-faceted effective chain of evidence, carrying out targeted prevention and control and risk control, reducing the difficulty of public security management for grassroots governments and their dispatched agencies, and improving the public’s sense of security.
Therefore, the construction of grassroots intelligent data centers not only helps to improve the efficiency of social public management, but also improves the service level of grassroots police officers, ultimately achieving sustainable development, and meeting the objective requirements of urban development.